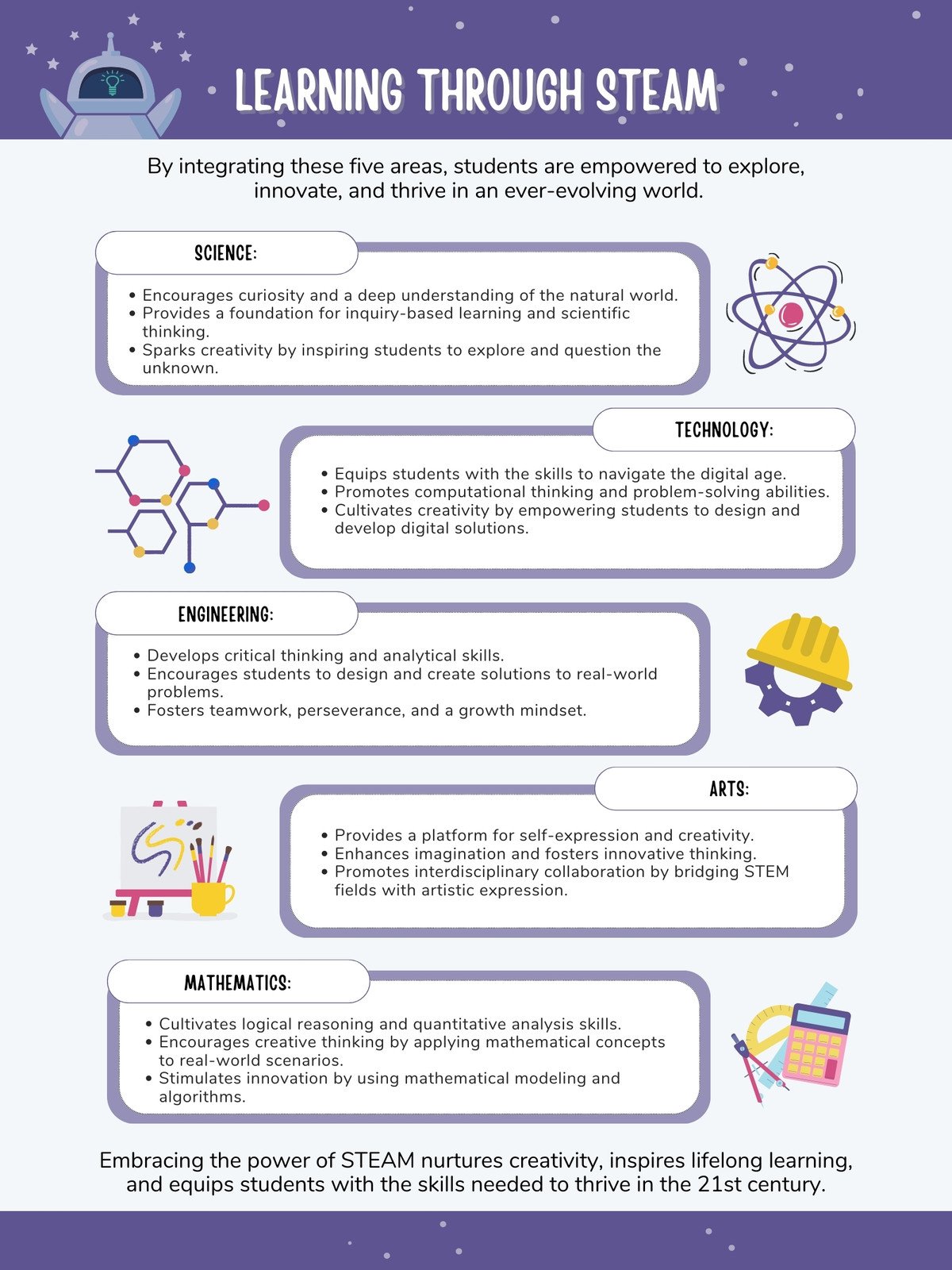
AI in Cybersecurity: Fortifying Defenses Against Emerging Threats


- Behavioral analysis of network traffic
- Detection of unusual user activity
- Identification of malicious code patterns
- Automated security monitoring and reporting
Detection Method | Description | Benefits |
|---|---|---|
Signature-based | Matches known malware signatures | Simple, fast detection |
Heuristic-based | Analyzes file behavior | Detects new malware variants |
AI-based | Uses machine learning to identify anomalies | Adaptive, high accuracy |
Detection Method | Description | Benefits |
|---|---|---|
Signature-based | Matches known malware signatures | Simple, fast detection |
Heuristic-based | Analyzes file behavior | Detects new malware variants |
AI-based | Uses machine learning to identify anomalies | Adaptive, high accuracy |

- Automated isolation of infected systems
- Dynamic firewall rule adjustments
- Automated log analysis and correlation
- AI-driven security orchestration
Response Stage | AI Role | Benefits |
|---|---|---|
Detection | Identify anomalous activity | Faster threat discovery |
Analysis | Determine severity and scope | Accurate risk assessment |
Containment | Isolate infected systems | Prevent lateral movement |
Remediation | Restore systems to a secure state | Minimize downtime |
Response Stage | AI Role | Benefits |
|---|---|---|
Detection | Identify anomalous activity | Faster threat discovery |
Analysis | Determine severity and scope | Accurate risk assessment |
Containment | Isolate infected systems | Prevent lateral movement |
Remediation | Restore systems to a secure state | Minimize downtime |

- Vulnerability scanning and patching
- Threat intelligence analysis
- Simulation of attack scenarios
- Proactive risk mitigation
Predictive Technique | Data Source | Benefit |
|---|---|---|
Threat Intelligence | Vulnerability databases, security blogs | Identify known vulnerabilities |
Behavioral Analysis | User activity logs, network traffic | Detect insider threats |
Machine Learning | Historical incident data | Forecast future attack trends |
Predictive Technique | Data Source | Benefit |
|---|---|---|
Threat Intelligence | Vulnerability databases, security blogs | Identify known vulnerabilities |
Behavioral Analysis | User activity logs, network traffic | Detect insider threats |
Machine Learning | Historical incident data | Forecast future attack trends |

- Automated vulnerability scans
- Risk-based vulnerability prioritization
- Patch management automation
- Compliance reporting
Vulnerability Type | AI Detection Method | Remediation |
|---|---|---|
Software Bugs | Static code analysis | Patch installation |
Configuration Errors | Automated configuration audits | Security policy enforcement |
Zero-Day Exploits | Behavioral anomaly detection | Virtual patching |
Vulnerability Type | AI Detection Method | Remediation |
|---|---|---|
Software Bugs | Static code analysis | Patch installation |
Configuration Errors | Automated configuration audits | Security policy enforcement |
Zero-Day Exploits | Behavioral anomaly detection | Virtual patching |

- Data privacy and security
- Algorithm transparency and explainability
- Bias mitigation in AI models
- Skill gap in AI cybersecurity expertise
Challenge | Mitigation Strategy | Benefit |
|---|---|---|
Bias | Diverse training data, algorithm auditing | Fair and accurate security decisions |
Transparency | Explainable AI techniques, clear documentation | Increased trust and accountability |
Privacy | Anonymization, data minimization | Protection of user data |
Challenge | Mitigation Strategy | Benefit |
|---|---|---|
Bias | Diverse training data, algorithm auditing | Fair and accurate security decisions |
Transparency | Explainable AI techniques, clear documentation | Increased trust and accountability |
Privacy | Anonymization, data minimization | Protection of user data |