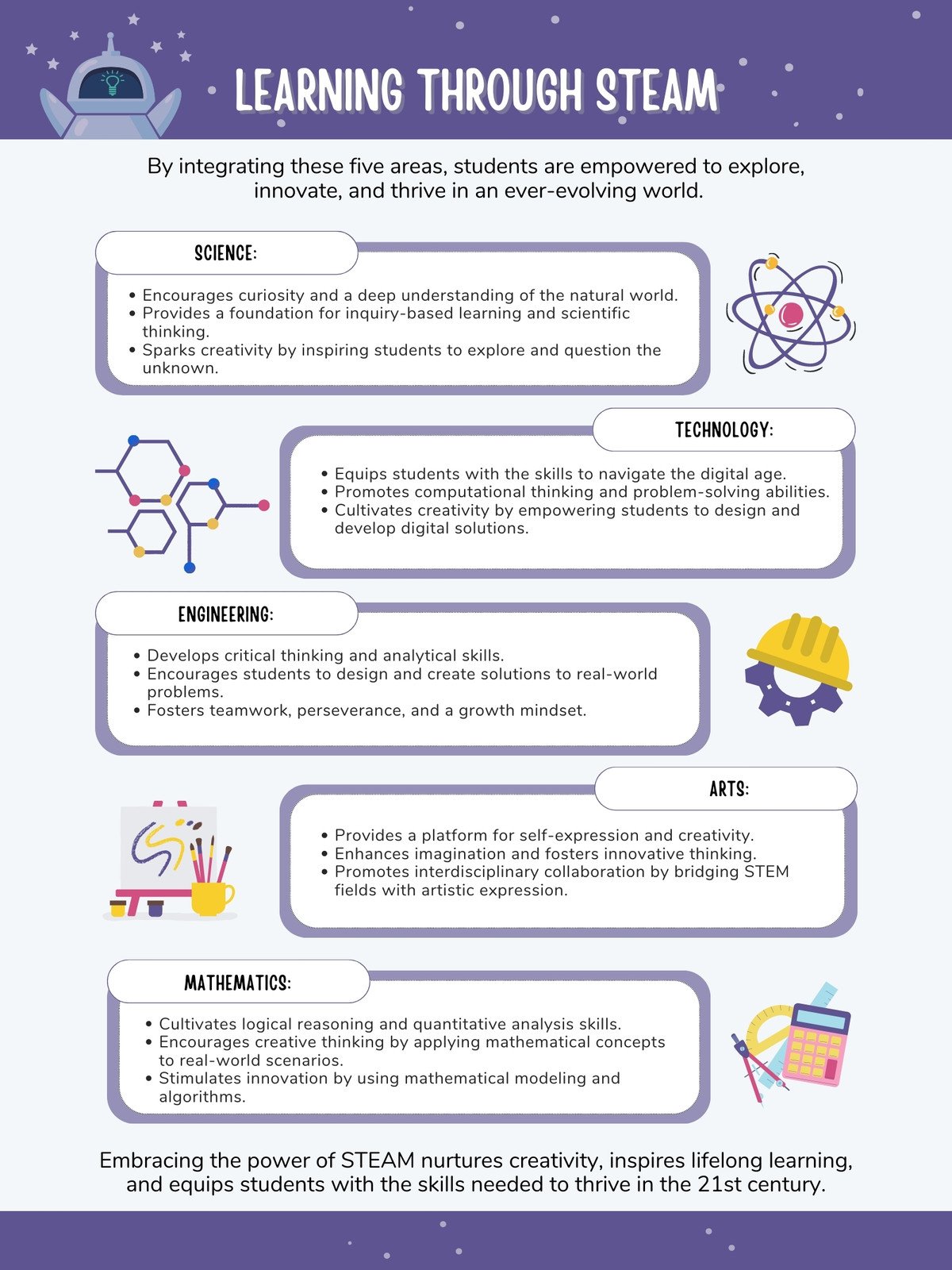
Cybersecurity Risk Assessment: A Step-by-Step Guide to Vulnerability Mitigation



- Hardware (servers, workstations, network devices)
- Software (operating systems, applications, databases)
- Data (customer data, financial records, intellectual property)
- Personnel (employees, contractors, vendors)
- Physical Infrastructure (data centers, offices)
Asset | Description | Value (Impact) |
|---|---|---|
Customer Database | Contains sensitive customer information | High |
Financial Server | Processes financial transactions | Critical |
Company Website | Provides information and services to customers | Medium |
Employee Laptops | Used for daily business operations | Medium |
Asset | Description | Value (Impact) |
|---|---|---|
Customer Database | Contains sensitive customer information | High |
Financial Server | Processes financial transactions | Critical |
Company Website | Provides information and services to customers | Medium |
Employee Laptops | Used for daily business operations | Medium |
- Malware (viruses, worms, ransomware)
- Phishing attacks (email, social media)
- Denial-of-service (DoS) attacks
- Insider threats (malicious or accidental)
- Data breaches (unauthorized access to sensitive data)
Threat | Description | Potential Impact |
|---|---|---|
Ransomware | Encrypts files and demands ransom for decryption key | Data loss, financial loss, reputational damage |
Phishing | Deceives users into revealing sensitive information | Data breach, identity theft, financial loss |
DDoS Attack | Overwhelms system with traffic, causing service disruption | Loss of productivity, revenue loss, reputational damage |
Insider Threat | Employee intentionally or unintentionally compromises security | Data breach, financial loss, legal penalties |
Threat | Description | Potential Impact |
|---|---|---|
Ransomware | Encrypts files and demands ransom for decryption key | Data loss, financial loss, reputational damage |
Phishing | Deceives users into revealing sensitive information | Data breach, identity theft, financial loss |
DDoS Attack | Overwhelms system with traffic, causing service disruption | Loss of productivity, revenue loss, reputational damage |
Insider Threat | Employee intentionally or unintentionally compromises security | Data breach, financial loss, legal penalties |

- Outdated software with known vulnerabilities
- Weak passwords and authentication mechanisms
- Misconfigured firewalls and network devices
- Lack of security awareness training for employees
- Unsecured data storage and transmission practices
Vulnerability | Description | Severity |
|---|---|---|
Unpatched Software | Outdated software versions with known security flaws | High |
Weak Password Policy | Lack of strong password requirements and enforcement | Medium |
Open Ports | Unnecessary open ports on network devices | Medium |
Lack of Employee Training | Insufficient security awareness training for employees | Low |
Vulnerability | Description | Severity |
|---|---|---|
Unpatched Software | Outdated software versions with known security flaws | High |
Weak Password Policy | Lack of strong password requirements and enforcement | Medium |
Open Ports | Unnecessary open ports on network devices | Medium |
Lack of Employee Training | Insufficient security awareness training for employees | Low |

- Likelihood (High, Medium, Low)
- Impact (High, Medium, Low)
- Risk level (High, Medium, Low)
- Mitigation priority (Critical, High, Medium, Low)
Threat | Vulnerability | Likelihood | Impact | Risk Level |
|---|---|---|---|---|
Ransomware | Unpatched Software | High | High | High |
Phishing | Lack of Employee Training | Medium | Medium | Medium |
DDoS Attack | Open Ports | Low | High | Medium |
Insider Threat | Weak Password Policy | Medium | High | High |
Threat | Vulnerability | Likelihood | Impact | Risk Level |
|---|---|---|---|---|
Ransomware | Unpatched Software | High | High | High |
Phishing | Lack of Employee Training | Medium | Medium | Medium |
DDoS Attack | Open Ports | Low | High | Medium |
Insider Threat | Weak Password Policy | Medium | High | High |
- Implement firewalls and intrusion detection systems
- Enable multi-factor authentication
- Develop and enforce strong password policies
- Provide security awareness training to employees
- Implement data encryption and access controls
Risk | Mitigation Strategy | Priority | Status |
|---|---|---|---|
Ransomware | Patch software regularly, implement anti-malware, backup data | Critical | In Progress |
Phishing | Provide security awareness training, implement email filtering | High | Completed |
DDoS Attack | Implement DDoS protection services, configure firewalls | Medium | Planned |
Insider Threat | Implement strong access controls, monitor user activity | High | In Progress |
Risk | Mitigation Strategy | Priority | Status |
|---|---|---|---|
Ransomware | Patch software regularly, implement anti-malware, backup data | Critical | In Progress |
Phishing | Provide security awareness training, implement email filtering | High | Completed |
DDoS Attack | Implement DDoS protection services, configure firewalls | Medium | Planned |
Insider Threat | Implement strong access controls, monitor user activity | High | In Progress |